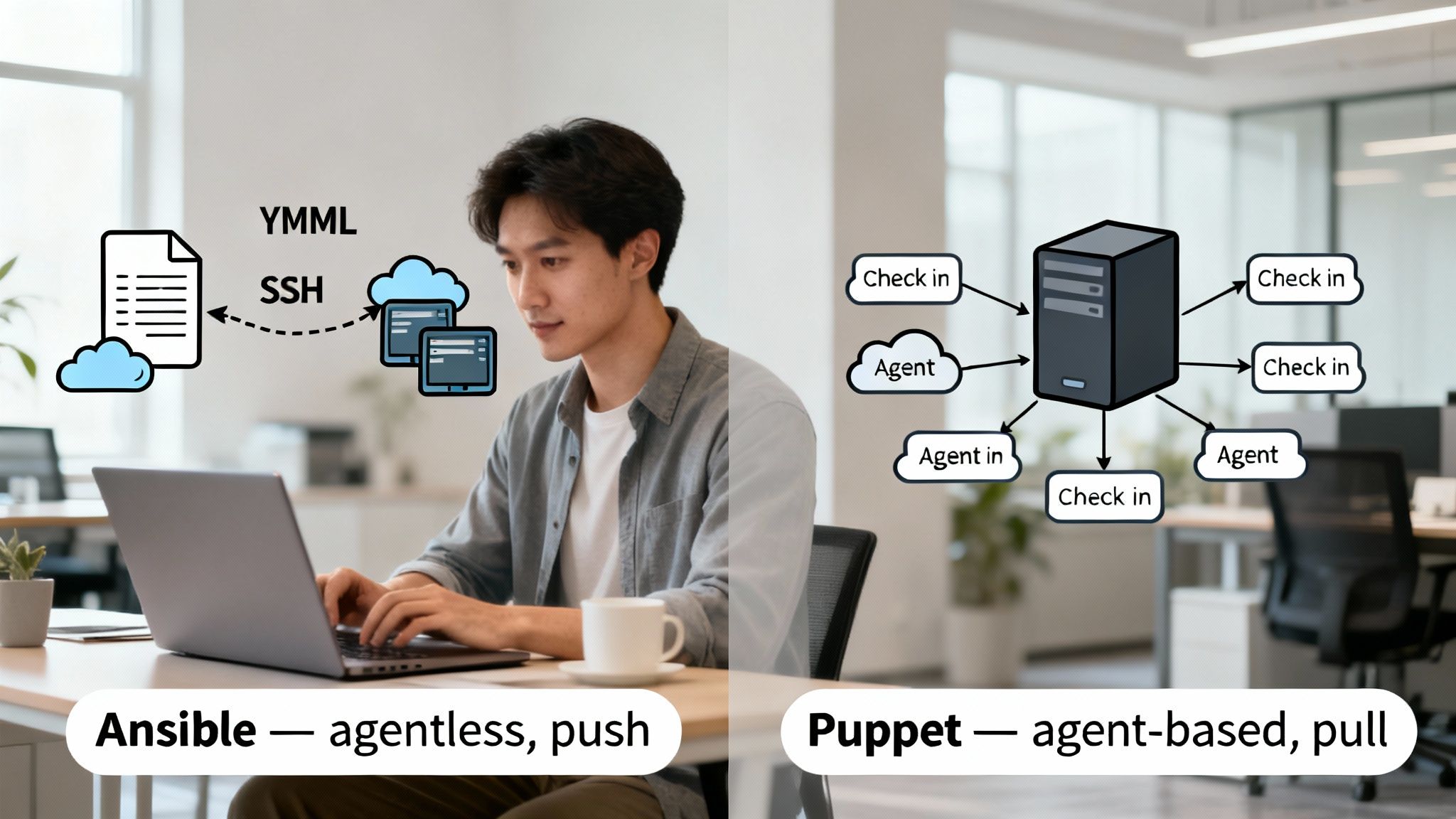
The Ansible vs Puppet debate is a pivotal decision for any DevOps team, and it hinges on a single strategic question: are you prioritizing speed and flexibility or control and consistency? Ansible's agentless, push-based architecture is engineered for the dynamic, on-demand nature of modern cloud environments. In contrast, Puppet’s agent-based, pull model provides the robust, declarative state enforcement required for large-scale, stable infrastructure where compliance is non-negotiable.
Understanding The Core Differences
Choosing the right configuration management tool is a business-critical decision that directly impacts operational efficiency, deployment speed, and infrastructure stability. While both Ansible and Puppet automate infrastructure, their foundational philosophies are fundamentally different, tailoring them to distinct operational needs and business goals.
Foundational Philosophies: Procedural vs. Declarative
Ansible operates procedurally. Its YAML-based "playbooks" define a sequence of tasks that Ansible executes in a specific order over SSH. This approach is intuitive for anyone familiar with scripting, making it ideal for application deployments, multi-step orchestration, and ad-hoc command execution. The business benefit is clear: faster time-to-value for task-oriented automation.
Puppet, conversely, is declarative. Using its model-based Domain-Specific Language (DSL), you define the desired end state of your infrastructure, not the steps to get there. The Puppet agent on each server then autonomously enforces that state, correcting any configuration drift. This is the gold standard for maintaining long-term consistency and proving compliance in highly regulated industries like finance, government, or healthcare.
To understand how these tools fit into a broader strategy, our DevOps tools comparison provides essential context.
The Business Impact of Ease of Use
Ansible holds a distinct advantage in usability. Its human-readable YAML syntax and agentless model can reduce the learning curve for new team members by 50-70%. Since its 2012 release, Ansible has empowered engineers to execute playbooks in minutes without installing client software on target nodes. This provides a significant ROI in dynamic environments like Kubernetes clusters or ephemeral cloud instances where agility is paramount.
Puppet, established in 2005, relies on a master-agent architecture and its own DSL. While this declarative model is incredibly powerful, it presents a steeper learning curve. Industry benchmarks show it can take 20-30 hours more training per engineer to achieve proficiency. You can read more on these benchmarks and their impact for a complete analysis.
Ansible vs Puppet At a Glance
This table provides a concise, side-by-side comparison of the core attributes of each tool.
| Attribute | Ansible | Puppet |
|---|---|---|
| Architecture | Agentless (Push-based via SSH) | Agent-based (Pull-based via Agent/Master) |
| Language | YAML (Procedural) | Puppet DSL & YAML (Declarative) |
| Primary Use Case | Application deployment, orchestration, ad-hoc tasks | Long-term state enforcement, compliance |
| Learning Curve | Low; easy for sysadmins to adopt | Steeper; requires learning a specific DSL |
| State Management | Mostly stateless; checks current state on-the-fly | Stateful; maintains a desired state catalog |
In summary, Ansible delivers speed and simplicity for task-based automation, while Puppet offers the rigorous, state-driven control essential for enterprise-grade consistency and compliance.
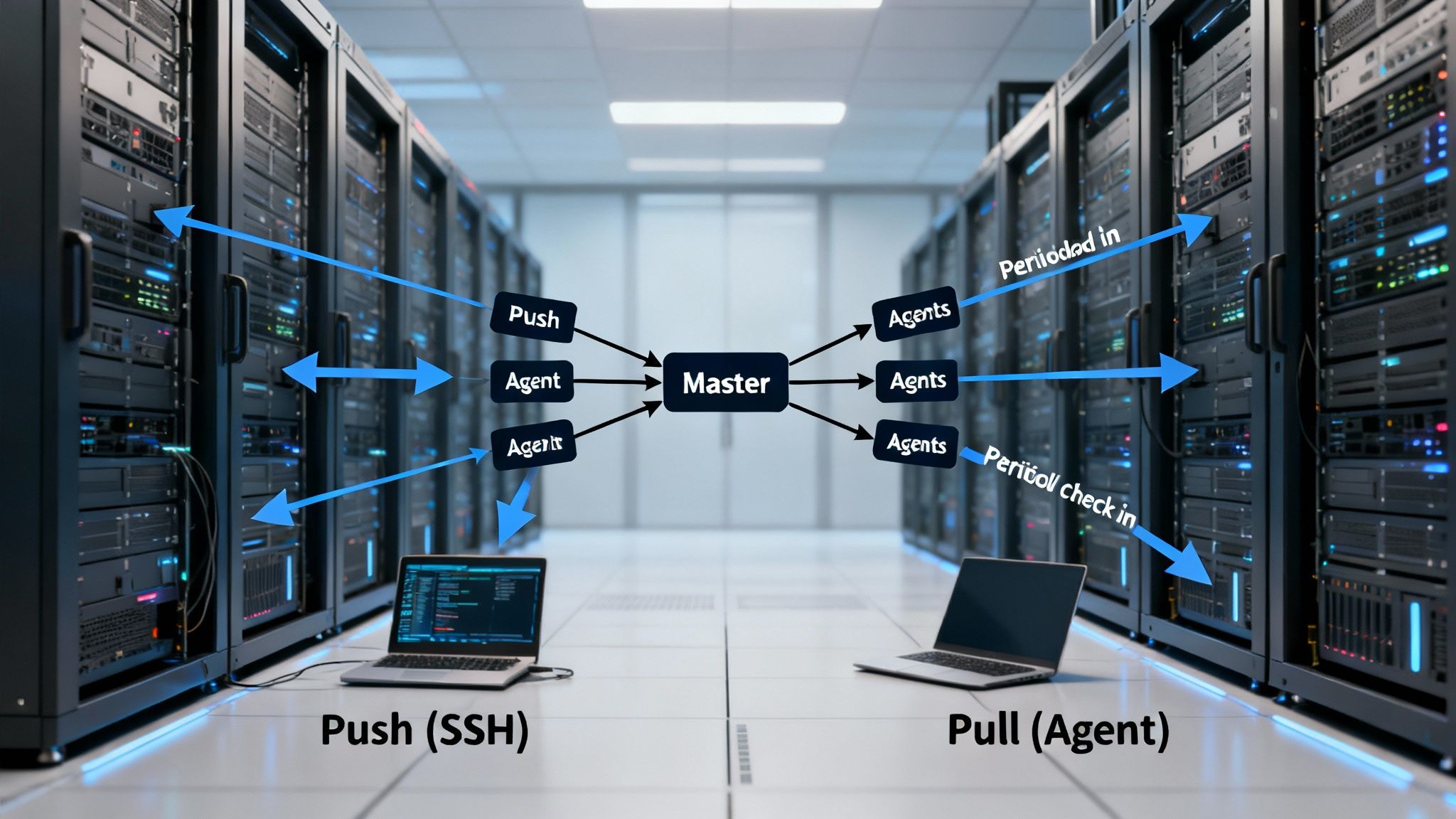
Comparing The Push vs Pull Architectures
A configuration management tool's architecture dictates its communication methods, scalability, and responsiveness. The most significant differentiator in the Ansible vs Puppet comparison is this: Ansible uses an agentless, push-based system, while Puppet employs an agent-based, pull model. This choice fundamentally shapes everything from initial setup and security posture to daily operational workflows.
Ansible's Push Architecture: A Model for Speed and Agility
Ansible’s architecture is designed for simplicity and immediacy. It utilizes a push model, where a central control node sends instructions to managed servers, typically over SSH for Linux or WinRM for Windows. Because no special software must be pre-installed on target machines, it is agentless.
This design is transformative for dynamic, fast-paced environments.
- Rapid Onboarding: New servers with SSH access can be managed instantly. This eliminates agent installation and configuration delays, making it ideal for cloud and on-premise environments.
- Reduced Overhead: With no agent consuming resources in the background, managed nodes are lighter. This is a significant advantage for lean infrastructure like containers or short-lived serverless functions.
- Smaller Attack Surface: Removing a resident agent eliminates a potential security vulnerability. All communication originates from a single, hardened control node.
Business Impact: Ansible's push model excels where speed and flexibility are primary business drivers. This includes application deployments, ad-hoc security patching, and managing ephemeral cloud instances that are frequently created and destroyed.
Puppet's Pull Architecture: A Foundation for Consistency and Control
Puppet uses a pull architecture built on a Master-Agent model. A Puppet agent is installed on every managed server. This agent periodically—typically every 30 minutes—checks in with a central Puppet Master to request its configuration instructions.
During each check-in, the agent downloads its latest configuration catalog. It then compares this "desired state" with its current state. If a discrepancy exists, the agent automatically remediates the drift, bringing the node back into compliance.
This model provides a distinct set of business advantages.
- Guaranteed State Enforcement: Continuous, agent-driven checks ensure configurations remain consistent, automatically correcting unauthorized changes without manual intervention.
- High Scalability and Reliability: The pull model distributes the workload. Each agent initiates its own check-in, reducing network bottlenecks and enhancing reliability, even over unstable connections.
- Centralized Control and Auditing: The Puppet Master serves as a single source of truth, enabling robust control and detailed reporting—a non-negotiable for compliance in regulated industries.
The market has responded to these architectural differences. Ansible's agentless model helped it capture nearly 50% of the market share by 2019, as it allowed companies to reduce deployment overhead by 30-50%. For more context, see the full market share analysis on Incredibuild. However, for organizations where absolute consistency and auditability are paramount, Puppet’s architecture remains the proven choice. Explore practical Infrastructure as Code examples to see these architectures in action.
Analyzing Usability And The Learning Curve
A tool's true power is only realized if a team can use it effectively. The learning curve of Ansible or Puppet directly impacts team productivity, training budgets, and time-to-value. The primary distinction is language: Ansible uses human-readable YAML, while Puppet uses its own Domain-Specific Language (DSL).
Ansible: The Fast Track to Automation
Ansible's use of YAML, with its simple key-value structure, makes it accessible to a broad audience, including sysadmins, network engineers, and junior DevOps staff. This procedural logic offers significant business advantages.
- Rapid Proficiency: Teams can become productive with Ansible in days. A junior engineer can write a basic playbook to install software or manage users without extensive training.
- Democratized Automation: Because it doesn't require deep programming skills, more technical staff can contribute, preventing automation from becoming an expert-only silo.
- Lower Training Costs: The investment in training time and resources is significantly reduced, making Ansible a compelling choice for startups and SMBs.
For a SaaS company needing to rapidly configure cloud servers for a new product launch, Ansible enables them to become operational quickly and efficiently.
Puppet: An Investment in Deep Expertise
Puppet's DSL is declarative and model-driven, rooted in Ruby. You don't script the steps; you define the ideal state of a system, and Puppet’s agent determines how to achieve and maintain it.
Key Differentiator: Ansible tells a system how to perform a task. Puppet tells it what the end state must be. This declarative model is extremely powerful for ensuring consistency but requires a deeper understanding of Puppet's syntax and logic.
This approach inherently involves a steeper learning curve. Engineers must master the Puppet DSL, resource abstraction concepts, and the Master-Agent architecture.
- Requires Specialized Skills: Effective Puppet implementation often requires dedicated experts or a significant investment in team training.
- Longer Time-to-Value: A team new to Puppet will take longer to write their first manifests and realize a return on their automation efforts.
- Powerful Abstractions (The Payoff): The DSL enables the creation of powerful, reusable modules that can manage highly complex environments with minimal code—a game-changer for large enterprises.
For a large financial institution where compliance is paramount, the strict control offered by Puppet's DSL justifies the learning curve. The ability to enforce a compliant state across a massive server fleet outweighs the initial training investment.
Evaluating Scalability and Performance Under Pressure
For any growing enterprise or SaaS platform, scalable automation is a core business requirement. A configuration management tool's performance under load dictates your ability to deploy new services, manage traffic spikes, and maintain stability. The architectural DNA of Ansible and Puppet defines their scalability profiles.
Ansible's agentless architecture has been proven to manage over 100,000 hosts from a single control node, which led to a 40% reduction in infrastructure costs for Red Hat post-acquisition. Meanwhile, Puppet's multi-master setup has supported operations at Google's exabyte scale since 2007, achieving 99.999% availability. For a deeper look, you can explore these scalability metrics and their implications.
Ansible for Horizontal and On-Demand Scaling
Ansible is designed to scale horizontally. Its push-based, agentless model is a natural fit for dynamic cloud environments where infrastructure is ephemeral. For platforms like AWS or Azure, Ansible's dynamic inventories are a key feature, allowing it to query a cloud provider's API for a real-time list of active nodes.
This makes it ideal for:
- Rapid Deployments: An e-commerce platform can use Ansible to deploy a new application version across hundreds of web servers in minutes.
- Ad-Hoc Task Execution: A security team can use Ansible to push a critical patch to thousands of servers immediately.
- Rolling Updates: Ansible can orchestrate complex, multi-tier application updates with zero downtime by updating nodes in controlled batches.
However, Ansible's push model performance is bound by the control node's capacity to manage simultaneous SSH connections. At massive scale, a tool like Ansible Automation Platform (AAP) is often required to distribute the workload.
Puppet for Large-Scale State Enforcement
Puppet was engineered to manage massive, long-lived server fleets with absolute consistency. Its multi-master architecture is designed for high availability and load distribution. In a large-scale deployment, multiple "compile masters" serve agent requests, preventing any single point of failure or bottleneck.
Key Insight: The Puppet vs Ansible comparison at scale highlights a fundamental difference: Puppet's pull model decentralizes execution, allowing the system to scale smoothly as nodes are added without overloading a central server.
This makes Puppet the optimal tool for:
- Compliance in Finance: A major bank can use Puppet to enforce an audited security configuration across tens of thousands of servers, ensuring continuous PCI DSS compliance.
- Data Center Management: A government agency can use Puppet to maintain a standardized operating environment across a vast on-premise data center, automatically correcting configuration drift.
While Puppet's initial setup is more complex, its architecture provides a more predictable and resilient performance profile for managing enormous infrastructures where stability and compliance are the primary objectives.
The Ecosystem: Community and Enterprise Support
A tool's value extends beyond its features to its supporting ecosystem. When evaluating Ansible vs Puppet, their community and enterprise support systems are just as important as their technical architectures.
Ansible benefits immensely from its acquisition by Red Hat, which has cultivated a large and active open-source community. This provides a vast repository of shared knowledge and pre-built automation.
Ansible Galaxy and Red Hat Support
The core of Ansible’s community is Ansible Galaxy, a public repository containing thousands of community-built roles and collections. These reusable automation blueprints cover everything from provisioning a web server to deploying a complex application, dramatically accelerating development.
For enterprise needs, Red Hat offers the Ansible Automation Platform (AAP). This commercial offering includes:
- Certified Content Collections: Secure, vetted, and fully supported modules.
- Full Enterprise Support: Direct access to Red Hat's technical experts.
- Advanced Features: A centralized UI, automation analytics, and role-based access controls for managing automation at scale.
This dual ecosystem provides a clear adoption path: start quickly with open-source community resources and scale to the secure, supported AAP environment as business needs evolve.
Puppet Forge and Perforce Enterprise Solutions
As a pioneer in the space, Puppet has a mature and robust ecosystem. Its community hub, the Puppet Forge, hosts over 7,000 modules, many of which are officially supported by Puppet or verified by partners, ensuring a high degree of trust for enterprise use. This is a primary resource for managing standard infrastructure like databases and network hardware. Our guide to DevOps as a Service explores how to leverage such ecosystems for business results.
Commercially, Puppet is part of Perforce, which offers Puppet Enterprise. This platform is designed for large organizations where security and compliance are paramount. Key features include:
- Continuous Compliance: Automatically enforce and report on configurations to meet strict regulatory standards.
- Impact Analysis: Preview the effect of code changes before deployment to prevent outages.
- Vulnerability Remediation: Rapidly identify and patch security vulnerabilities across the entire infrastructure.
Both platforms offer strong support. Ansible provides a massive, fast-moving community backed by Red Hat for enterprise needs. Puppet delivers a stable, mature ecosystem with a focus on verified modules, supported by Perforce’s powerful compliance and risk management tools.
How To Choose The Right Tool For Your Business
The choice between Ansible and Puppet is a strategic business decision. The right tool depends on your team's skills, infrastructure, and strategic goals. It’s not about which tool is better, but which is the best fit for the job.
For fast-moving tech companies and product teams, speed and simplicity are paramount. Ansible’s agentless, push-based model is ideal for rapid application deployments and iterative changes, aligning perfectly with agile development methodologies.
Conversely, large enterprises in regulated sectors like finance, government, or healthcare operate under different constraints. For them, stability, security, and compliance are non-negotiable. Puppet’s declarative, model-driven architecture is engineered for this environment, providing robust, continuous enforcement of a desired state.
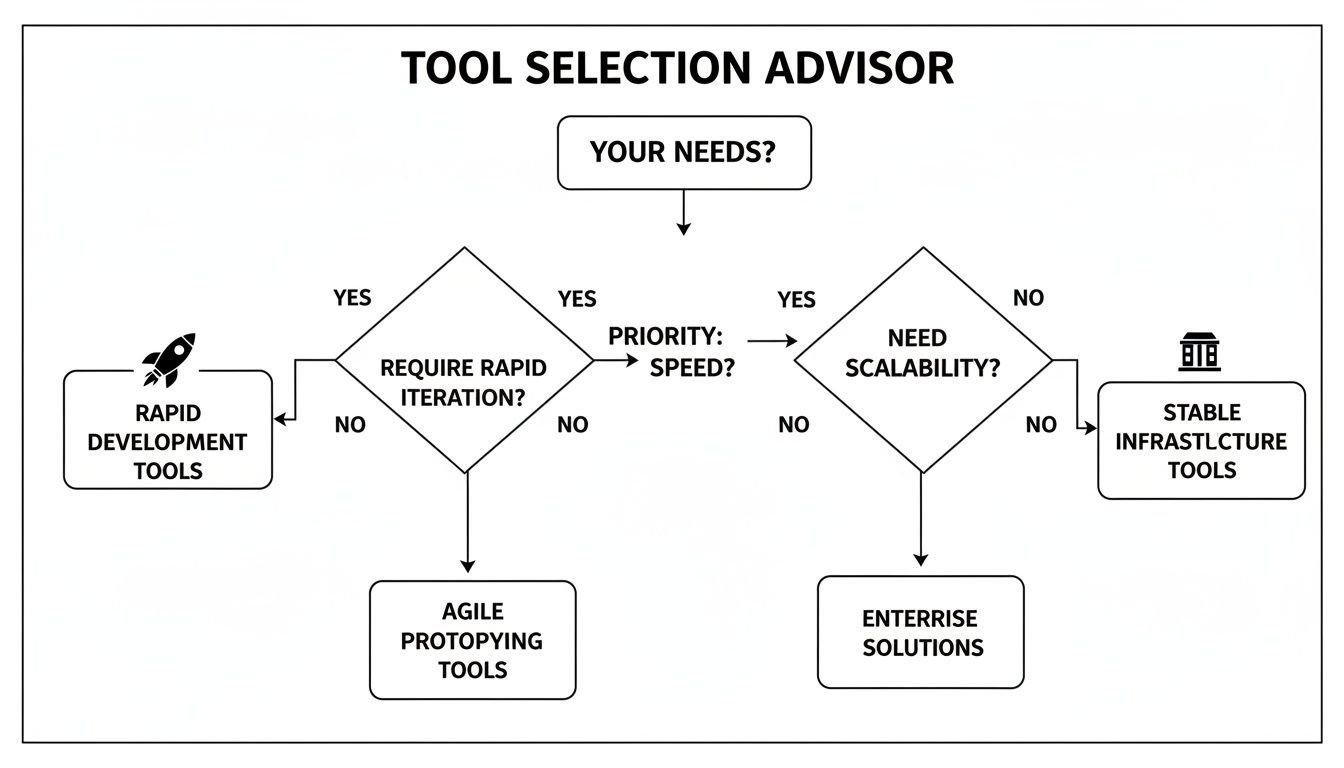
This decision tree illustrates the core tradeoff: optimizing for rapid iteration versus stable, long-term infrastructure management.
If your priority is rapid development, the path leads to Ansible. If unbreakable infrastructure stability is the goal, Puppet is the logical choice.
A Practical Decision-Making Checklist
To make an informed decision, work through these key questions with your stakeholders.
- What are your team's existing skills? If your team is proficient in scripting and YAML, Ansible will have a lower learning curve. If you have developers with Ruby experience or a team willing to learn a DSL for more powerful abstractions, Puppet is a strong contender.
- What does your infrastructure look like? For dynamic, ephemeral cloud environments, Ansible’s agentless model is more efficient. For stable, long-lived server fleets, Puppet’s agent-based model delivers superior consistency.
- What are your primary use cases? For application deployments and specific, one-off tasks, choose Ansible. For long-term state enforcement and automatic remediation of configuration drift, choose Puppet.
- What are your security and compliance needs? Puppet's model-driven approach and detailed reporting are purpose-built for environments with strict regulatory requirements.
- What is your long-term strategic goal? To empower a wide range of staff to automate tasks quickly, choose Ansible. To build a centralized team of experts managing a complex, standardized environment, the investment in Puppet will yield greater long-term control.
Decision Matrix: Ansible vs. Puppet Use Cases
This table maps common business scenarios to the recommended tool.
| Use Case / Industry | Recommended Tool | Key Reason |
|---|---|---|
| Early-Stage Startup | Ansible | Speed to market is critical; agentless simplicity allows for rapid iteration. |
| CI/CD Application Deployment | Ansible | Excels at push-based, procedural tasks perfect for pipeline integration. |
| Financial Services / Banking | Puppet | Provides strong, auditable enforcement of configuration for compliance. |
| Government / Public Sector | Puppet | Model-driven approach ensures strict policy and security baselines are met. |
| Multi-Cloud Management | Ansible | Agentless nature makes it easier to manage dynamic, heterogeneous cloud nodes. |
| Large-Scale Data Centers | Puppet | Agent-based model is ideal for managing thousands of stable, long-lived servers. |
| Short-Term Projects / POCs | Ansible | Low barrier to entry and quick setup make it perfect for temporary initiatives. |
Summary and Next Steps
The Ansible vs Puppet choice is strategic. Ansible is your tool for agility and speed, perfect for accelerating time-to-market. Puppet is your tool for control and consistency, essential for managing enterprise-scale infrastructure with unwavering reliability.
To contextualize how these tools drive modern software delivery, explore our guide on "What is a CI/CD pipeline?" and see how automation fuels the entire process.
Your next steps should be:
- Assess Your Team and Infrastructure: Use the checklist above to evaluate your current capabilities and operational needs.
- Define Your Primary Goal: Clearly identify whether your main objective is speed of deployment or long-term state enforcement.
- Run a Proof of Concept (POC): Test your chosen tool on a small, non-critical project to validate its fit and performance in your environment.
Ready to build a scalable, high-performance infrastructure with the right automation strategy? Group 107 provides expert DevOps as a Service to streamline your CI/CD pipelines, optimize cloud operations, and accelerate your time to market.
Learn how our dedicated engineering teams can transform your vision into reality.