When it comes to digital security, the debate over AES vs. RSA isn't about picking a winner—it's about understanding their distinct, complementary roles. In short, AES uses a single secret key to encrypt and decrypt data, making it incredibly fast for protecting large volumes of information. RSA uses a public/private key pair, a slower but essential method for securely exchanging that secret key and verifying identity over untrusted networks.
The critical takeaway for any business leader, developer, or product manager is this: you don't choose one over the other. You leverage both to build a robust, layered security strategy. Understanding when and how to deploy each is fundamental to protecting sensitive data and maintaining customer trust.
The Core Difference: AES vs. RSA
For businesses operating in high-stakes industries like SaaS, finance, or e-commerce, mastering the application of AES and RSA is non-negotiable. These two algorithms are not competitors; they are partners that form the backbone of modern data protection.
Think of AES as the high-security vault door. It's engineered for one job: protecting massive amounts of data with extreme efficiency. This makes it the go-to standard for encrypting entire databases, large files, and real-time network traffic where performance is paramount.
RSA, in contrast, is the secure courier service. Anyone with a public address (the public key) can send a locked box (an encrypted AES key), but only the authorized recipient with the unique private key can open it. This process is slower by design but is the only reliable way to establish trust and securely exchange the keys to the vault.
Symmetric vs. Asymmetric Encryption: The Foundational Models
AES and RSA are built on two different cryptographic principles. Understanding the distinction between symmetric and asymmetric key encryption is crucial for applying them correctly.
- AES (Symmetric): Uses the same secret key for both encryption and decryption. This simplicity is its greatest strength, enabling high-speed performance.
- RSA (Asymmetric): Relies on a mathematically linked public/private key pair. Data encrypted with the public key can only be decrypted by the corresponding private key.
The demand for robust encryption is accelerating. The global data encryption market was valued at USD 10.82 billion in 2023 and is projected to reach USD 27.04 billion by 2033. The banking and financial services sector alone accounted for over 21% of that market in 2023, underscoring the critical business need for these technologies.
AES vs. RSA: At a Glance
This table provides a clear, high-level comparison of how the two encryption standards stack up.
| Attribute | AES (Advanced Encryption Standard) | RSA (Rivest-Shamir-Adleman) |
|---|---|---|
| Encryption Type | Symmetric (single shared key) | Asymmetric (public/private key pair) |
| Primary Business Use | Encrypting large volumes of data (bulk data encryption) | Secure key exchange and digital signatures |
| Performance | Extremely fast and computationally efficient | Significantly slower and resource-intensive |
| Key Size | 128, 192, or 256 bits | Typically 2048 bits or higher (e.g., 3072, 4096) |
In practice, you rarely use just one. Modern security protocols like TLS/SSL (the "S" in HTTPS) use a hybrid approach. RSA initiates the secure "handshake" to safely agree upon a temporary AES key. Once that key is exchanged, all subsequent communication is encrypted with the much faster AES algorithm. This hybrid model delivers the best of both worlds: the verifiable trust of RSA and the high-performance data protection of AES.
How AES Symmetric Encryption Powers Data Protection
When protecting massive datasets—whether at rest on a server or in transit across a network—performance is critical. This is where AES (Advanced Encryption Standard) excels. As a symmetric algorithm, AES is the industry's undisputed workhorse, engineered for speed without compromising security.
AES operates as a block cipher, processing data in fixed 128-bit chunks and scrambling each block through a series of complex mathematical rounds. This systematic and efficient process makes it incredibly fast, capable of securing terabytes of data with minimal computational overhead.
The primary advantage of AES in the AES vs. RSA comparison is its raw velocity. Because it uses the same shared key to encrypt and decrypt, the process is orders of magnitude faster than any asymmetric algorithm. For any application where high throughput is a business requirement, AES is the only practical choice.
Key Sizes and Their Business Implications
The strength of an AES implementation is determined by its key size. Product managers and engineers must select the right size based on data sensitivity and compliance requirements.
- AES-128: The baseline for solid security and excellent performance. Ideal for general-purpose encryption where speed is the top priority.
- AES-192: An intermediate option, but less common in practice. Most organizations either select AES-128 for speed or advance directly to AES-256 for maximum security.
- AES-256: The gold standard for security. Mandated for protecting top-secret government data, sensitive financial records, and mission-critical intellectual property. While marginally slower than AES-128, the difference is negligible on modern hardware.
Upgrading from a 128-bit to a 256-bit key exponentially increases the difficulty of a brute-force attack. It's a strategic trade-off: a minuscule performance cost for a monumental leap in security. Strong encryption is a core component of a holistic security strategy; our guide on how to prevent website hacking covers other essential layers.
Expert Insight: For any fintech, SaaS, or enterprise application handling sensitive data, implement AES-256 by default. The security assurance it delivers far outweighs the negligible performance impact, especially when measured against the catastrophic cost of a data breach.
Business Case: AES in a High-Volume Fintech Application
Consider a fintech platform that processes thousands of payment transactions per second. Each record contains sensitive PII and financial details that must be encrypted at rest to comply with standards like PCI DSS.
Using a slow encryption algorithm would introduce unacceptable latency, degrading the user experience and potentially causing transactions to fail. The system must encrypt data on write and decrypt it on read instantly and seamlessly.
This scenario is a perfect use case for AES. Its efficiency enables the platform to manage high throughput while maintaining ironclad security. By implementing AES-256, the company achieves critical business outcomes:
- Minimize Latency: Ensures encryption and decryption operations never become a performance bottleneck, maintaining fast response times.
- Reduce Computational Costs: Lowers the CPU load for cryptographic tasks, translating directly to reduced server costs and more efficient infrastructure.
- Meet Compliance Requirements: Satisfies stringent industry mandates for strong data encryption without sacrificing system performance.
Ultimately, AES enables businesses to protect data at scale, ensuring that security supports—rather than hinders—the performance of mission-critical systems.
How RSA Asymmetric Encryption Establishes Trust
While AES is the workhorse for encrypting data, RSA (Rivest-Shamir-Adleman) is the diplomat that enables the secure initial handshake. It serves a different but equally vital role: establishing a trusted channel so high-speed encryption can begin. As an asymmetric algorithm, RSA uses a pair of mathematically linked keys—one public, one private.
The concept is elegant and powerful. Data encrypted with a public key can only be decrypted by its corresponding private key. This one-way function creates the foundation of digital trust, allowing two parties to initiate a secure conversation without ever sharing a secret key over an insecure network like the internet.
When we compare AES vs. RSA, we see they aren't designed for the same task. RSA’s purpose is not to encrypt gigabytes of data; it is to securely deliver the small, single-use AES key that will.
The Public-Private Key Pair in Action
Think of RSA’s public key like a mailbox with an open slot. Anyone can deposit an encrypted message, but only the individual with the unique physical key (the private key) can open the box and read its contents.
- Public Key: Distributed openly. You can post it on your website, include it in an email signature, or embed it in a digital certificate. Its sole function is to encrypt data intended for you.
- Private Key: Your most critical secret. It must be guarded relentlessly, as it is the only key that can decrypt data encrypted with its public counterpart. If your private key is compromised, the entire trust model collapses.
This model also powers digital signatures. By "signing" data with your private key, you create a verifiable mark that proves the data originated from you and has not been tampered with. Anyone with your public key can verify the signature, confirming both authenticity and integrity.
Prime Factorization: The Math Behind RSA Security
RSA’s security is rooted in a computationally difficult mathematical problem: prime factorization. The algorithm generates its keys by multiplying two extremely large prime numbers to create an even larger public number.
The brilliance of this design is its asymmetry: multiplying the two primes is easy for a computer, but reversing the process—factoring the large public number back into its original primes—is practically impossible for even the most powerful supercomputers. The keys used in RSA-2048 are so large that it would take billions of years to brute-force the factors.
Key Takeaway: The staggering difficulty of factoring large numbers gives RSA its strength. This computational imbalance is why we trust it for mission-critical tasks like authentication and secure key exchange.
Business Case: RSA in the TLS/SSL Handshake
You see this process every time you visit a secure website. The padlock icon in your browser signifies a successful TLS/SSL handshake, where RSA plays a critical opening role. Encrypting the entire session with RSA would be unacceptably slow, so it is used only for the crucial first step.
Here’s a simplified breakdown of the process:
- Server Presents Certificate: Your browser connects to the server, which provides its SSL certificate containing its public key.
- Browser Verifies and Encrypts: Your browser validates the certificate. It then generates a new, single-use symmetric key (an AES key).
- Secure Key Exchange: Your browser uses the server's public RSA key to encrypt the new AES key and sends it back to the server.
- Server Decrypts: The server uses its private RSA key to decrypt the package and retrieve the shared AES key.
- Secure Session Begins: With a shared secret AES key, both parties switch to high-speed symmetric encryption for all further communication.
This hybrid model leverages the strengths of each algorithm. RSA establishes trust and securely exchanges a key, while AES takes over for high-volume, high-performance data transfer.
Comparing Performance, Security, and Key Management
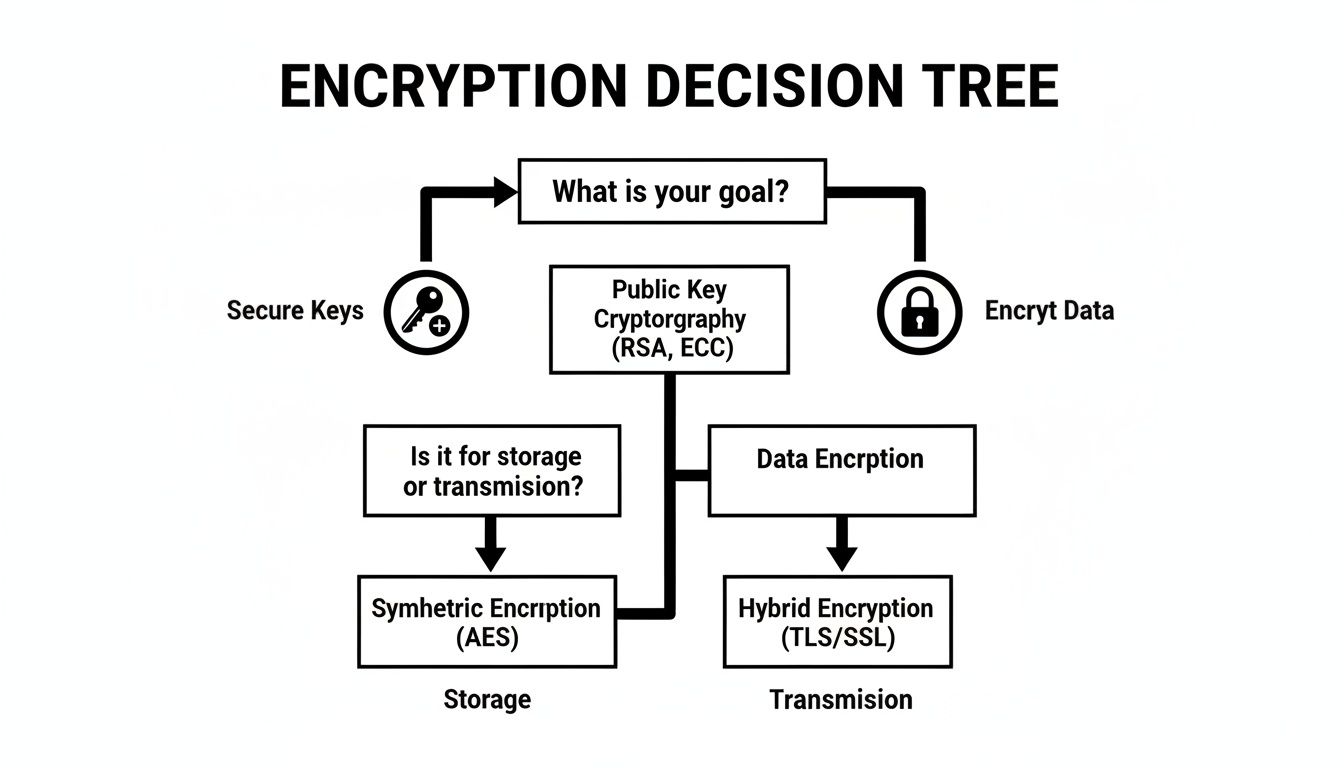
When choosing between AES and RSA, the decision hinges on three factors: performance, security strength, and the complexity of key management. These algorithms were designed for different purposes. The AES vs. RSA discussion is not about which is superior, but which is the right tool for the specific business objective.
This decision tree clarifies the process: use AES for the heavy lifting of data encryption and RSA to protect the AES keys themselves.
As the chart illustrates, your primary goal—protecting data or protecting keys—determines the correct cryptographic path.
Performance Benchmarks and Business Impact
The performance difference between AES and RSA is stark. AES is built for speed, using simple algebraic operations that are highly optimized in modern hardware. RSA, in contrast, performs complex modular exponentiation on very large numbers, making it computationally intensive.
This speed differential has significant business implications:
- Bulk Data: Encrypting a 1 GB file with AES takes seconds. The same operation with RSA would take hours, if not days, and would overwhelm the CPU. This makes AES the only viable choice for databases, file storage, and real-time data streams.
- Initial Handshakes: RSA’s slower speed is acceptable for its specific, limited role: securely exchanging a small amount of data, such as an AES key, during a TLS handshake. The one-time performance cost is a small price for establishing a secure channel.
Expert Insight: Never use RSA for bulk data encryption. Its sole purpose is to establish trust and securely transfer a symmetric key for an algorithm like AES. Misusing RSA for bulk data will create a severe performance bottleneck that will cripple your application.
This technical benchmark comparison highlights why these algorithms are not interchangeable.
Technical Benchmark: AES vs. RSA
| Metric | AES | RSA | Business Impact |
|---|---|---|---|
| Algorithm Type | Symmetric (one shared key) | Asymmetric (public/private key pair) | AES is optimized for internal efficiency, while RSA enables secure public key sharing without pre-existing trust. |
| Performance | Extremely fast (hardware accelerated) | Very slow (computationally intensive) | AES is essential for high-throughput systems (databases, APIs). RSA is only practical for small, infrequent operations like key exchange. |
| Key Size | 128, 192, 256 bits | 2048, 3072, 4096 bits | AES keys are compact and efficient. RSA keys are much larger, impacting storage and transmission overhead. |
| Primary Use Case | Bulk data encryption (data-at-rest, data-in-transit) | Key exchange, digital signatures | AES protects the actual data. RSA protects the key used to encrypt that data. |
| Key Management | Secure key distribution is the primary challenge. | Protecting the private key is paramount. | The choice dictates security architecture: AES needs a secure channel, while RSA creates one. |
This table makes it clear: these algorithms solve different problems. AES provides high-speed data protection, while RSA provides a mechanism to establish trust in untrusted environments.
Security Strength and Key Equivalency
While both algorithms are considered secure when implemented correctly, their security is derived from different mathematical principles. AES security is based on its resistance to brute-force attacks. RSA’s strength comes from the computational difficulty of factoring large prime numbers.
Because of these differences, an RSA key must be significantly larger to provide the same level of security as an AES key.
- An AES-128 bit key is considered equivalent in strength to an RSA-3072 bit key.
- An AES-256 bit key's strength is comparable to a massive RSA-15360 bit key.
This size disparity is why RSA keys are so large—they must be to make prime factorization infeasible with current and near-future computing power. You can see these hybrid encryption principles in practice when comparing various VPN protocols like OpenVPN and IKEv2.
The Challenge of Key Management
Effective key management is often more challenging than the encryption itself and is a common point of failure in security architectures.
AES Key Management:
The primary challenge with AES is secure key distribution. Since the same key is used to encrypt and decrypt, you must have a secure method to share that key with authorized parties. If an attacker intercepts the key, all data encrypted with it is compromised. This is precisely why AES is almost always paired with an asymmetric algorithm like RSA for the initial key exchange.
RSA Key Management:
With RSA, key distribution is simple—broadcast the public key freely. However, the focus shifts entirely to protecting the private key. If the private key is leaked, the security of the entire system is compromised. Additionally, verifying that a public key genuinely belongs to its claimed owner requires a Public Key Infrastructure (PKI) and digital certificates.
Choosing the Right Algorithm for Real-World Scenarios
Applying AES and RSA effectively means moving from theory to practical implementation. This isn't about choosing the "best" algorithm—it's about selecting the right tool for a specific business need. For teams building enterprise SaaS, fintech platforms, or secure DevOps pipelines, knowing when to use each is foundational to a strong security posture.
The AES vs. RSA decision ultimately comes down to one question: are you protecting a large volume of data, or are you establishing a trusted channel to share a small secret?
When to Use AES for Bulk Data Encryption
AES is the workhorse of encryption, built for speed and efficiency. It is the definitive choice for protecting data at scale, both at rest and in transit.
Actionable use cases for AES include:
- Encrypting Databases with PII: A fintech platform storing Personally Identifiable Information (PII) must encrypt database tables. AES-256 with transparent data encryption (TDE) secures customer data without impacting application performance.
- Securing Files in Cloud Storage: When uploading sensitive documents or backups to services like AWS S3 or Azure Blob Storage, AES is the standard for both server-side and client-side encryption, providing a critical layer of defense against credential compromise.
- Protecting API Data Payloads: For SaaS applications exchanging sensitive data via APIs, encrypting request and response bodies with AES ensures data confidentiality as it travels between microservices or to a client.
The shift to cloud-native infrastructure makes efficient encryption more critical than ever. The cloud segment captured over 61% of the encryption software market in 2023. You can discover more insights about encryption market trends that highlight this widespread adoption.
When to Use RSA for Trust and Key Exchange
RSA is slower but performs the unique and vital job of establishing trust and securely exchanging secrets over untrusted networks. Its asymmetric design is ideal for any scenario where pre-sharing a key is not feasible.
Actionable use cases for RSA include:
- Creating Digital Signatures: A software company signs a new product update with its private RSA key. Users can verify the signature with the public key, confirming the update is authentic and has not been tampered with.
- Enabling Secure HTTPS Connections: As discussed, the TLS/SSL handshake relies on RSA. The browser uses a server's public key to encrypt a temporary AES key, which then secures the rest of the session.
- Encrypting Secrets in DevOps: In a CI/CD pipeline, secrets like API keys and database credentials must be protected. RSA is ideal for encrypting these secrets so that only authorized servers with the private key can decrypt and use them during deployment.
The Hybrid Model: How AES and RSA Work Together
In any modern security system, you almost never choose one or the other. Instead, AES and RSA are combined in a powerful hybrid encryption model that provides the best of both worlds.
Here is a step-by-step framework of the hybrid model:
- Key Generation: The sender generates a new, random symmetric key (an AES key) for one-time use.
- Bulk Encryption: The sender uses the high-speed AES key to encrypt the large dataset or message.
- Key Wrapping: The sender encrypts the small AES key using the recipient's public RSA key.
- Secure Transmission: Both the AES-encrypted data and the RSA-encrypted AES key are sent to the recipient.
- Unwrapping and Decryption: The recipient uses their private RSA key to decrypt the wrapped AES key. With the original AES key now securely recovered, they can efficiently decrypt the entire dataset.
This hybrid approach allows RSA to handle the secure exchange of a small secret, while AES performs the high-speed encryption of the actual data. Combining these tools is essential for a layered defense, a concept detailed in our guide to the best data security technologies to avert cyber threats.
Implementation Best Practices and Common Pitfalls
Selecting the right algorithm is only the first step. Secure implementation is where success or failure is determined. Even the strongest algorithms are useless if deployed incorrectly. For engineering and product teams, best practices mean using vetted libraries, implementing robust key management, and avoiding common, costly mistakes.
The foundation of secure implementation is using well-maintained, industry-standard cryptographic libraries. Never attempt to write your own cryptography.
- General Purpose: OpenSSL provides robust, battle-tested implementations of both AES and RSA.
- Java/JVM: Bouncy Castle offers a comprehensive suite of cryptographic APIs.
- Python: The cryptography library is the modern, high-level choice for simplified and secure implementation.
Using these libraries is not a shortcut; it is a critical step to avoid introducing vulnerabilities that experts have already solved.
Avoiding Common Implementation Errors
Most security breaches result not from cryptographic breakthroughs but from simple implementation flaws. In the context of AES vs. RSA, several common mistakes recur.
For AES, the most critical error is using the wrong mode of operation. Electronic Codebook (ECB) mode is insecure because it encrypts identical plaintext blocks into identical ciphertext blocks, creating patterns that attackers can exploit. Always use authenticated encryption modes like GCM (Galois/Counter Mode) or CCM, which provide both confidentiality and integrity. Another common error is reusing Initialization Vectors (IVs) with the same key, which completely undermines security.
For RSA, the primary threats are padding oracle attacks. These exploits allow an attacker to decrypt messages by observing how a server responds to malformed requests. To prevent this, always use modern padding schemes like OAEP (Optimal Asymmetric Encryption Padding). As our guide on REST API security best practices explains, secure data handling extends beyond algorithm choice.
Expert Insight: Implementation details are often more critical than the choice of algorithm. A properly implemented AES-128 in GCM mode is far more secure than a poorly configured RSA-4096 implementation vulnerable to side-channel attacks.
Secure Key Management and Rotation
Your encryption is only as strong as your key management. Keys must be securely managed throughout their entire lifecycle: generation, storage, usage, and destruction. Storing keys in configuration files or hardcoding them in source code is a recipe for a data breach.
Implement a dedicated key management solution:
- Cloud-Based: AWS Key Management Service (KMS) or Azure Key Vault are managed services that simplify key creation and control.
- On-Premises/Hybrid: HashiCorp Vault is a powerful solution for centralizing secrets and key management across complex, multi-cloud environments.
Finally, implement key rotation. Regularly changing cryptographic keys limits the potential damage if a key is ever compromised. A robust key management system automates this process, ensuring your security posture remains strong over time.
Summary and Next Steps
The AES vs. RSA debate is not about choosing a single winner. It's about strategically applying the right tool for the right job to build a comprehensive security framework.
Key Takeaways:
- AES is for Data: Use AES for high-speed, bulk encryption of data at rest and in transit. It is the workhorse for protecting databases, files, and API traffic. For maximum security, default to AES-256.
- RSA is for Keys: Use RSA to establish trust and securely exchange keys. Its primary roles are enabling the initial TLS handshake and creating digital signatures to verify authenticity and integrity.
- Hybrid is the Standard: Modern security relies on a hybrid model where RSA securely encrypts and transmits an AES key, and AES handles the actual data encryption.
Actionable Next Steps:
- Audit Your Current Implementations: Review your systems to ensure you are using AES for bulk data and RSA for key exchange and signatures. Verify that you are not using RSA to encrypt large data payloads.
- Validate Your Libraries and Configurations: Confirm you are using up-to-date, vetted cryptographic libraries. Ensure AES is implemented with a secure mode like GCM and RSA is using a secure padding scheme like OAEP.
- Strengthen Your Key Management: If you are not already using a dedicated Key Management System (KMS) like AWS KMS, Azure Key Vault, or HashiCorp Vault, prioritize its implementation. Establish and automate a key rotation policy.
- Prepare for a Post-Quantum Future: While AES-256 is considered quantum-resistant, RSA is not. Begin tracking the development and standardization of Post-Quantum Cryptography (PQC) algorithms to inform your long-term security roadmap.